Mobile network security offer opportunities
Updated: 2013-09-18 11:16Beijing - International Data Corporation (IDC), a provider of market analysis for IT industry, expects China IT security market to experience a year-on-year growth of 12.7% in 2013 to reach a market size of $1,830 million.
In line with the forecast, IDC predicts that the compound growth rate of China IT security market from 2012 to 2017 will reach 12.2%.
According to IDC's research, China IT security market reached $1,660 million in 2012, an increase of 12.9% year-on-year.
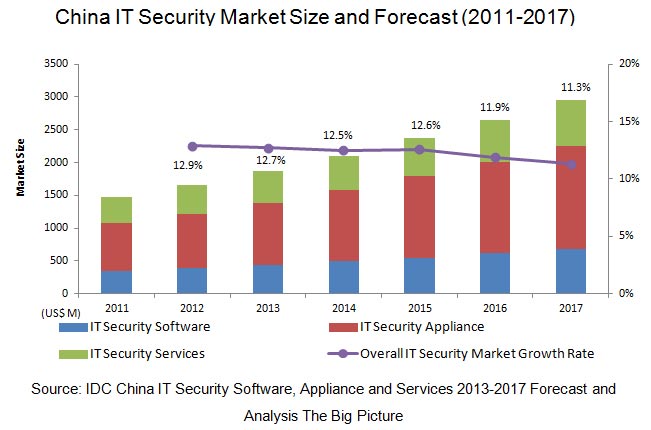
The security appliance market at $830 million, accounted for 51.3%, while the security service and software market accounted for 24.5% and 24.3% respectively.
Due to an overall slowdown in economic growth, multiple fields in the IT industry experienced slow growth in 2012, however, the IT security market maintained a rapid growth.
"Compared with developed countries, China's IT security investment in 2012 only accounted for 1% of the overall IT industry; in addition, influenced by the recent ‘Prism' event, the government is expected to issue new security policies to protect the national information security system," says Pei Wang, Research Manager responsible for IT Security Market Research in IDC China.
He notes that at the same time, customer demand for IT security is increasing continuously, therefore, China IT security market has a great potential for future growth.
"Emerging technologies for the third IT platform including cloud computing, big data, mobile and social network will lead the future growth of the IT security field.”
As cloud computing matures, the internal resources in the current data center are increasingly virtualized, and the physical-based traditional protection mechanism is unable to effectively protect user applications and information security under the shared virtualization environment. That leads to separation of ownership and management right of information, making unauthorized access to information assets a serious security problem for the cloud computing system.